- Specialized High Defense Servers
Fast & Secure 
 High-End Dedicated Servers
High-End Dedicated Servers
We provide high-performance, highly reliable, and secure servers with 24/7 localized support.

Choose the high-defense server that suits you
Choose Now







Choose Now







Choose Now







Choose Now







Choose Now














Need help? View the full program or contact our online customer service
Pre-installed environment for free
Professional Team Dedicated to solving problems for you
























- Dedicated Server Hosting
Limited Time Offer
Why choose 08Host?

High availability
Equipped with the new-generation multi-core processors and enterprise-level storage architecture, it achieves the processing capability of millions of concurrent requests and microsecond-level response speed. It adopts CN2/BGP intelligent scheduling and connects to the Chinese mainland at high speed with low latency
high reliability
Advanced Tier3+ data center, dual-active hot standby cluster architecture and full-link redundancy design, a 99.999% availability commitment, along with 7×24 expert-level operation and maintenance, ensure that business continuity meets financial-grade standards
high security
Adopt a five-layer collaborative defense system, integrate T-level full-protocol DDoS protection, use AI for intelligent identification of CC attacks, and embed a Web application firewall to build a full-stack security defense line from the network boundary to data storage
24/7 Customer Support
Multi-language 24/7 online support from a team of professional server technicians!

Online Chat
Multi-channel live chat support

call center
9:00 a.m. to 8:00 p.m.

Sales Team
+852 1633 082
Build locally, publish globally
In addition to being a well-known high-end service provider hosting provider in Hong Kong, we are also a Google Cloud Global Premium Reseller.









What our customers say about us
Affordable and trustworthy
I've been doing web development for 10 years and I've always chosen 08HOST. their servers are affordable and extremely secure, and after-sales service is extremely efficient with no work orders to submit and direct online support.
Trgdv Hosfbt
DeveloperPerfect load capacity
Carrying 800,000 live streaming traffic and DDoS attacks at the same time, the bandwidth elasticity has been expanded 18 times without triggering manual approval - this automated defense system definitely has black technology! Peers are asking which server we use!
Carrie Royjh
Co-ArchitectThe best game server hosting provider in my opinion
Since migrating to 08host, we are very satisfied with the smooth operation of Immortal OL, which has 3 million simultaneous online users, and the availability and security as well as cloud disaster recovery meet our requirements.
Car Roberts
Operations ManagerGreat discounts on Google Cloud
I purchased the google cloud server through 08Host, the discount is really great, and they helped me directly to configure the parameters, pre-installed the management panel, the service is especially thoughtful.

DTR berts
Ethical HackerThe best high-end service provider and hosting provider in Hong Kong

Enterprise-level server hosting solutions
O8HOST focuses on high-end server hosting in Hong Kong and is a well-known local IDC service provider in Hong Kong. It is also a global senior partner of Google Cloud, deeply integrates Google Cloud's native technology stack, and offers extreme discounts.
- CN2 GIA low latency direct connection to mainland China
- 1Tbps +BGP multi-line redundant network
- T-level all-protocol DDoS protection
- 99.91 TP3T Network Online Guarantee
- 4th Generation Xeon Gold Processors
- Enterprise SSD/M.2 NVMe Storage
- Kingston DDR5 RAM
- Hong Kong Tier 3+ Data Center
Game industry high defense CDN how to choose to protect the smooth operation of the game
To be honest, the experience of being paralyzed on the first day of the launch of our handheld game last year still haunts me when I think about it. Seeing the players crazy influx, the server suddenly stuck into PP [...]
Explore MoreHands-on with Linux Firewall Rules
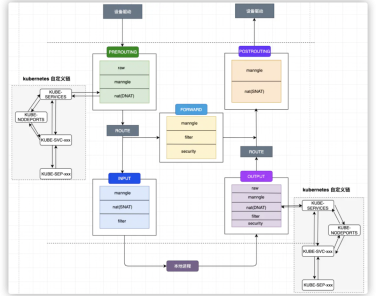
From K8s Troubleshooting to iptables In-Depth Analysis: Hands-On Linux Firewall Rules Background After dealing with a Kuber [...] yesterday.
Explore MoreHardware Firewall vs Software Firewall for High Defense Servers
Have you ever encountered website access suddenly slowed down, apps often down, or game servers "burst" at night? Behind these problems, you may not be the one who [...]
Explore MoreDo you have any questions about our high-defense servers?
Contact one of our technical consultants today. Our team is online 24/7 and ready to answer any questions you may have.
Server FAQ
A collection of frequent user questions and answers to efficiently answer your queries.
CN2 (China Telecom's Next Generation Carrier Network, AS4809) is a high-performance network of China Telecom, focusing on providing services for enterprises that need to establish efficient telecommunications connections with China, and achieving direct connections with major global ISPs through optical fiber data transmission. CN2 is divided into two types: International Internet Transit (CN2 GT) and International Internet Dedicated Line Access (CN2 GIA). Among them, CN2 GIA represents high-end services, providing the best performance and the lowest latency. Our servers use the higher-quality CN2 GIA network
We provide physical dedicated servers, not cloud servers. Some parameters support dynamic upgrades. If you need to upgrade the hardware, there may be a short downtime. For specific matters, please consult our online customer service
Yes, we support Usdt payments with no real name and no authentication.
We support 3-5 days free trial, payment after satisfactory trial. After payment, we do not support any kind of refund except our server abnormality.
High-defense server single 300G, protocol protection can be more than T level.
High-defense servers can effectively defend against the vast majority of DDoS attacks and common network attacks. However, for some complex attacks (such as zero-day attacks and specific attacks targeting the application layer), additional security measures may be required, such as using a Web Application Firewall (WAF), vulnerability scanning, etc