DDoS host
Hong Kong High Defense Anonymous Server
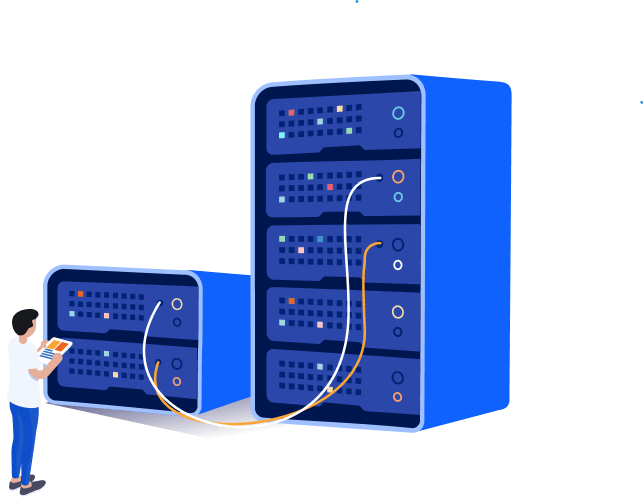
Hong Kong data center deployment of anonymous anti-DDoS hosting, support for USDT/BTC payment, to provide T-level traffic cleaning + intelligent WAF protection. 100% no-log policy, no need to record and real-name authentication, 5-minute high-speed opening.
Top Server Hosting Service Providers

Hostingard is rated 4.9/5 on Trustpilot

Hostingard is rated 4.9/5 on Trustpilot

Hostingard is rated 4.9/5 on Trustpilot

Hostingard is rated 4.9/5 on Trustpilot
Packages & Prices
We provide cost-effective solutions covering different protection levels and resource requirements. Whether it is the stable operation of the basic business, or to deal with large traffic attacks, support USDT convenient payment, instant access to exclusive anonymous anti-DDoS hosting services!
basic version
Entry-level choice for anonymous protection and stable performance$1500
$18000
Selected Services
- Gold 6138 * 80 cores
- 128G Memory
- 1T SSD Disk
- 50M CN2 bandwidth
- 10 IPs
- 100G DDOS Defense
advanced version
Advanced Protection for Medium-Scale Attack Challenges$2500
$30000
Selected Services
- Gold 6138 * 80 cores
- 128G Memory
- 1T SSD Disk
- 50M CN2 bandwidth
- 10 IPs
- 200G DDOS Defense
Enterprise Preferred
flagship edition
Top configuration, T-level protection to guard core business security$4500
$54000
Selected Services
- Gold 6138 * 80 cores
- 128G Memory
- 1T SSD Disk
- 100M CN2 bandwidth
- 10 IPs
- 300G DDOS Defense
Supreme Edition
Customized solutions to meet the demanding needs of mega-enterprises$7000
$84000
Selected Services
- Gold 6138 * 80 cores
- 128G Memory
- 1T SSD Disk
- 200M CN2 bandwidth
- 10 IPs
- 500G DDOS Defense
99.991 TP3T service availability
Automatic node failover, annual service interruption time <5 minutes
Financial-grade data security
AES-256 encryption is used for data storage, TLS1.3 protocol is enabled for transmission, and the server room has passed ISO27001 security certification.
24/7 professional technical support
Chinese and English technical team, Telegram, WhatsApp real-time response
Redefining the New Standard for Anonymous Anti-DDoS Hosting
From privacy protection to attack defense, from payment security to performance optimization, we use cutting-edge technology and extreme services to build an impenetrable network defense for you, and meet the multiple needs of global users for anonymity, security and efficiency.

Ultimate anonymity guaranteed
Multi-layer privacy encryption technology is used to hide the real IP and server information, and no logs are kept for the whole access. Combined with Tor network and onion routing technology, it prevents traffic tracking and ensures 100% anonymization of business data to meet the needs of privacy-sensitive users.

Super T-level DDoS protection
Deploying Hong Kong's top high defense nodes, with basic protection bandwidth starting from 200Gbps, which can be flexibly expanded to T-level. Real-time monitoring and cleaning of SYN Flood, UDP Flood, CC attacks and other 20+ types of attacks, intelligent AI algorithms to accurately identify malicious traffic, protection accuracy rate of up to 99.9%.

USDT anonymous payments are convenient and secure
Support USDT full chain payment (ERC20/TRC20/BEP20), no need for KYC authentication, transfer is activated. Based on blockchain technology to realize anonymous transactions, the flow of funds can not be traced, to protect the security of payment, while enjoying zero fee, seconds to the account experience.
Hong Kong Premium Node Extreme Response
Hong Kong data center directly connected to the CN2GIA line, Asia Ping value <20ms, Europe and the United States latency optimization 30%. BGP multi-line access, automatic adaptation of the global network, to ensure that the business of low-latency, high-stability operation.

Automated Intelligent Defense System
Integration of SOAR (Security Orchestration Automation and Response) platform, when an attack occurs, automatically performs a 12-step defense process, from traffic cleaning, IP blocking to vulnerability remediation, with an average response time of <5 seconds, which improves the efficiency of 80% over traditional manual processing.

Multilingual Global Technical Support
The Chinese and English technical team is on standby 24/7 and supports multi-channel communication such as Telegram, WhatsApp and work orders. No matter where you are in the world, you can get timely and professional solutions to any technical problems you encounter.

High cyber-attack protection with strong privacy features
DDoS attack protection: By deploying large bandwidth (usually up to 100Gbps or even Tbps level) and professional traffic cleaning equipment, real-time identification and filtering of SYNFlood, UDPFlood, CC attacks and other types of DDoS attack traffic, to ensure that servers can still run stably when subjected to large-scale attacks to ensure business continuity.
Privacy and anonymity protection: IP hiding technology, no logging policy and encrypted communication protocols (e.g. Tor network, onion routing, SSL/TLS encryption, etc.) are used to hide the user's real IP address and access logs, preventing the network traffic from being tracked and monitored, and ensuring the anonymity and privacy security of the user's identity, data transmission and business activities.
Get in touch today for a quick solution!
Hong Kong's Fortress of Anonymity: The Stealthy Guardian That Blocks 2 Million Attacks Per Second
We love our customers and they love us!
Excellent collaboration experience
This anonymous high-defense server perfectly solves the security risks of our cross-border business! 200G + protection bandwidth is easy to resist attacks, USDT payment is also very convenient, the technical team responds quickly, and the cooperation experience is excellent!
Mr. Lee
A cross-border technology limited companyThe cooperation experience is excellent!
The anonymous DDoS - protected server here perfectly resolved the security risks of our cross - border business! The 200G+ protection bandwidth easily withstands attacks, and

David Brown
Ocean Global Tech Co., Ltd.Quick response to the technical system.
The anonymous high-defense server in Kochira is a solution to the problem of cross-border networks' security concerns! Attacks on the 200G or higher bandwidth area are simply resisted, and payment by USDT is very convenient.
Suzuki Aiko
Sunrise International Trading Co.Stable operation, highly recommended
For our chess program, anonymity and security are crucial. This server not only has top anonymity protection technology, but also very reliable high defense capability. It has been used safely for more than 5 years, which guarantees the stable operation of nodes and is highly recommended!
Mr. Wang
An online chess operating companyFrequently Asked Questions (FAQ)
No, it won't. We use intelligent traffic cleaning technology, only intercept malicious attack traffic, normal user access will not be affected. At the same time, Hong Kong's high-quality nodes and CN2GIA lines to ensure low-latency, high-speed access.
After the USDT transfer is made and confirmed, the system will automatically activate the host within 5 minutes and send the login information via email.
Yes. We adopt no-log policy to not record any user access information, and at the same time, through multi-layer encryption and anonymization technology, to hide the real IP of the server and user operation traces, to maximize the protection of privacy and security.
Yes. Our AI-driven defense system is based on continuous learning from 20 billion+ attack samples, and can identify new types of attacks such as HTTP/3 traffic fragmentation and DNS reflection in real time, with protection policies automatically updated and an interception accuracy rate of 99.8%.
Particularly suitable for blockchain projects (smart contracts, wallet nodes), cross-border e-commerce independent sites, anonymous social platforms, online sports / chess applications, as well as enterprise or personal business with high requirements for privacy protection and network security.